- Security Suffix
- Secure Upgrade Procedure
- Upgrade Authentication
- Downgrade Restriction
- Tamper-proof Mechanism
Security Suffix
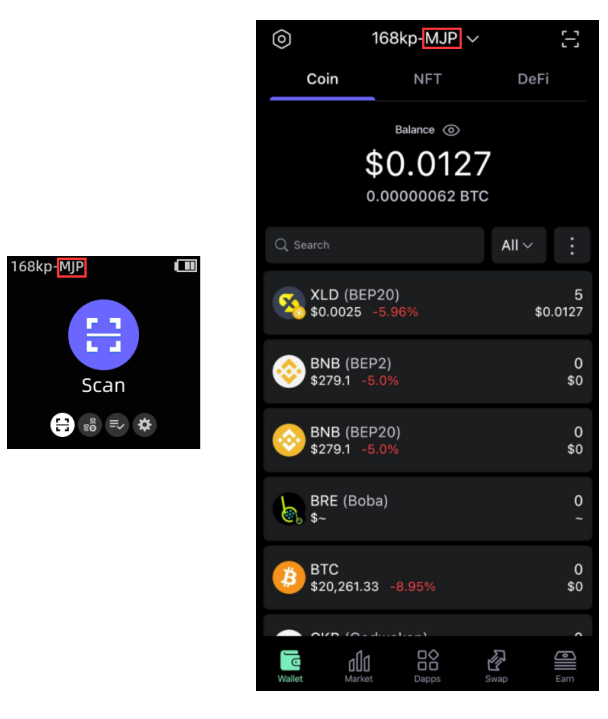
A Security Suffix is a combination of 3 characters(letters and numbers) displayed when you create a new wallet on the SafePal S1 hardware wallet or in the SafePal App. If you are using an S1 hardware wallet, when the S1 device is paired with the SafePal App, the security suffix will also be synced in the App, as shown in the picture below.
A Security Suffix of a SafePal wallet is generated based on your mnemonic phrase and device information and helps you to recognize a unique wallet from other wallets. If someone resets your S1 hardware wallet or software wallet by stealing your device, you can easily tell that the wallet has been changed, because the security suffix will be different on a new wallet. If you notice that the security suffix of your wallet has been changed, for asset security, please reset and recover your wallet with the correct mnemonic phrase.
Secure Upgrade Procedure
The firmware upgrade of the S1 hardware wallet is an important feature to allow users to update their S1 devices and enjoy the latest product features.
SafePal S1 is embedded with a firmware verification program that examines the genuineness of every uploaded firmware. And the device only runs official firmware released through the SafePal official website. If there is any malicious firmware loaded to the device, the device will show warnings.
Upgrade Authentication
Before you upgrade the S1 firmware, the PIN code must be entered for verification purposes.
Downgrade Restriction
SafePal only supports firmware upgrades rather than downgrades, thus protecting any potential attacks from the lower versions.
Tamper-proof Mechanism
Whenever an S1 hardware wallet is started, the multi-verification mechanism embedded in SafePal S1 will authenticate the complete program. Should there be any unauthorized changes detected during this process, even as small as a byte, the device will fail to start up normally, thus preventing any potential attacks from the supply chain or logistics scenarios.

